
Continuing the Security Tips series I started in July '13, today I wish to discuss with you all the topics listed after the following links. Just in case you want to access the last posts in this series, here are the links:
Part 1: General Guidelines - Click Here
Part 2: Microsoft Windows - Click Here
Part 3: Macintosh - Click Here
Part 4: Guest Accounts - Click Here
Part 5: Windows Firewall - Click Here
Part 6: Event Viewer & Netstat - Click Here
Part 7: Antiviruses - Click Here
Let's first consider in brief the structure of this post.
- Introduction
- What is encryption
- Objectives of Encryption
- Usage of Encryption
- Types of Encryption
- Symmetric v/s Asymmetric Key Encryption
- Encryption Standards
- Digital Certificates
- Digital Signatures
- Cryptography Tools
- TrueCrypt
- Conclusion/Comments
Introduction
Personal computers and portable computing devices often contain confidential data such as payment information, personal files, bank account details, and more, which must be shielded from prying eyes in the event of theft or loss of the device. I’ll be talking about encryption and how can we as users use this superb technique to protect our data.

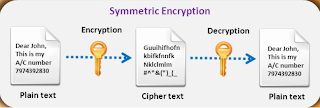
Plaintext: In cryptography, plaintext is the ordinary, readable text from before being encryption into cypher text and is the result of decryption.
Cipher Text: Cipher text is the encrypted text that is unreadable until it has been decrypted to plaintext with a key. It is used to securely send messages over the Internet.
Encryption Key: A key is a piece of information that can encrypt, decrypt, or perform both functions, depending on the type of encryption being used.
What is encryption
Encryption is the process of converting information, programs, images, and other data into an unreadable cipher text to prevent unauthorized access by applying a set of complex algorithms that transform the data into blocks or streams of random alphanumeric characters.
If Bob wants to send sensitive data to Alice, and wants to be sure that only Alice may be able to read it, he will encrypt the data with Alice's Public Key. Only Alice has access to her corresponding Private Key and as a result is the only person with the capability of decrypting the encrypted data back into its original form. As only Alice has access to her Private Key, it is possible that only Alice can decrypt the encrypted data. Even if someone else gains access to the encrypted data, it will remain confidential as they should not have access to Alice's Private Key. Thus cryptography secures the data against eavesdropping. We can also see it is irreversible since everyone knows public key to send the message, the private key to decrypt is known only to the receiver.

To add a digital signature to his message (which guarantees the originality of the sender), Bob does a compilation involving both his private key and the message. When the receiver, Alice, gets the message, she checks the digital signature to verify the origin of the message being genuine or not.
Objectives of Encryption
There are 3 major objectives:
- Confidentiality: is probably the most common aspect of information security. We need to protect our confidential information. An organization needs to guard against those malicious actions that endanger the confidentiality of its information. Confidentiality not only applies to the storage of the information, it also applies to the transmission of information. When we send a piece of information to be stored in a remote computer or when we retrieve a piece of information from a remote computer, we need to conceal it during transmission.
- Integrity: means that changes need to be done only by authorized entities and through authorized mechanisms. Integrity violation is not necessarily the result of a malicious act; an interruption in the system, such as a power surge, may also create unwanted changes in some information.
- Availability: The information created and stored by an organization needs to be available to authorized entities. Information is useless if it is not available. Information needs to be constantly changed, which means it must be accessible to authorized entities. The unavailability of information is just as harmful for an organization as the lack of confidentiality or integrity. Imagine what would happen to a bank if the customers could not access their accounts for transactions.
Usage of Encryption
- Encryption is used to protect user credentials such as user names and passwords.
- It helps to safely store sensitive information on a computer or external storage media.
- Encryption provides a secure medium for users to connect to their friends or employees’ networks from outside the home or office.
- It provides a higher level of trust when receiving files from other users by ensuring that the source and contents of the message are trusted.
- Encryption is used as a resource for web-based information exchange to protect important information such as credit card numbers.
- It provides assurance of a sender’s identity.
- Encryption helps avoiding attention to a confidential email.
Types of Encryption
- Symmetric Encryption: It is private key encryption technique which ensures privacy and confidentiality. Only one key is used for both encryption & decryption. It can be either block cipher or stream cipher.
- Asymmetric Encryption: It is public key encryption technique and ensures non-repudiation and user authentication. The user uses 2 keys, public key for encryption & private key for decryption.
- Hash Function: It ensures integrity, which is also referred to as one-way encryption and message digest. Hash functions are used by the operating systems to encrypt the passwords and ensure that files are not altered by unauthorized users.


Symmetric v/s Asymmetric Key Encryption
| Symmetric Key Encryption | Asymmetric Key Encryption |
| Symmetric encryption uses only one key for both encryption and decryption | Asymmetric encryption uses a public key for encryption & private key for decryption |
| The key cannot be shared safely | In asymmetric encryption, the public key can be freely shared, which eliminates the risk of compromising the secret key. |
| Symmetric encryption requires that the sender and the receiver of the data know the secret key | Only the public key is known |
| The algorithm is less complex & faster | Algorithm is slower & complex |
| The key length is fixed | The key length is variable |
| It is used for bulk encryption, i.e., for encrypting files & communication paths | It is used for key encryption & distribution |
| Symmetric encryption ensures confidentiality and integrity | Asymmetric encryption ensures confidentiality, authentication, non-repudiation, and integrity |
Encryption Standards
- DES
The data encryption standard is the name of the Federal Information Processing Standard (FIPS) 46-3, which describes the data encryption algorithm (DEA). The DES has a 64-bit block size and during execution it uses a 56-bit key. When it is used for communication, both the sender and he receiver must know the secret key that is used to encrypt and decrypt the message, or to generate and verify a message authentication code. It is a symmetric cryptosystem originally designed to be implemented in hardware. It is used for single-user encryption such as storing encrypted files on a hard disk. - AES
The advanced encryption standard is an iterated symmetric block cipher defined in FIPS, which means that it works by repeating the same defined steps multiple times. It is a secret key encryption algorithm, and operates on a fixed number of bytes. AES-128, AES-192, AES-256 are the three block cipher present in AES.
Digital Certificates
A digital certificate is an electronic card that provides credential information while doing business or other online transactions on the web. It contains the name, expiration date, signature information, and serial number, copy of the owner’s public key, and digital signature authentic. It is used to verify one’s identity and can be used in various ways such as to control access on websites, to secure email, to create virtual private networks, and to assure the authenticity of downloaded software. Digital certificates can be personal certificates, server certificates, or certificate authority certificate. Digital certificates are used for Identification, Authentication, and Security.
A user requests a certificate from a Registration Authority, which verifies the applicant, and requests the Certification Authority issues a certificate to the user. The Certification Authority issues a public key certificate to the user and sends the updated information to the Validation Authority, which is contacted by someone who wishes to verify the digital certificate of the user.
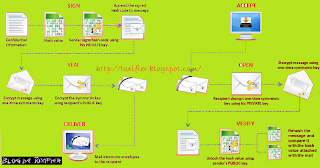
Digital Signatures
A digital signature is a cryptographic means of authentication. Public key cryptography, which uses an asymmetric key algorithm, is used to create the digital signature. The two types of keys in public key cryptography are the private key & the public key. “Hash function” is a process which is used when creating and verifying a digital signature. This algorithm creates a digital representation of a message, but is still unique. If any change is made to the message, it will automatically produce a different hash result; it is not possible to derive the original message from the hash value in case of a secure hash function, which is also known as “one-way hash”.
The hash result of the original message and the hash function that is used to create the digital signature are required to verify the digital signature. With the help of the public key and the new result, the verifier checks:
- If the digital signature is created with the related private key
- If the new hash result is the same as the original hash result, which was converted into a digital signature during the signing process
The certification authority digitally signs the certificate to assure the authenticity of both the public key and the subscriber’s identity. The authority’s digital signature on the certificate can be verified with the help of the public key of the certification authority recorded in another certificate, which belongs to another certification authority. This certificate can be authenticated with the help of another public key recorded in another certificate and so on.
The repository can be made to publish the certificate; the public key and its identity are available for verification of the certificate. The retrieval and verification of the digital signature is made with the help of online databases called repositories, which holds the certificates and other information. The certification authority may suspend or revoke the certificate.
Cryptography Tools
TrueCrypt
Since this post has already been quite long, I’ll discuss Cryptography Tools and TrueCrypt in my next post. Thank You!
Conclusion/Comments
I hope you find all the relevant information you must know about the topic of security I discussed with you all today. For any queries or suggestions please feel free to comment here.
I hope you all have a great day ahead! :) Happy Tuesday :) See you all soon! :D


No comments:
Post a Comment
Kindly keep the comments clean and make quality comments that would be worthy in making this blog better! :)